Phishing-Resistant Authentication: Embracing Passwordless in Microsoft Entra
/ in cybersecurity, Network & Information Security Liability, Compliance, Vulnerability Management, Audit Ready, CYBER SECURITY STRATEGY / by Boško Tasevski
Authentication methods have evolved significantly in response to the threat landscape. Traditional password-based authentication once considered the bedrock of digital security, now faces formidable challenges, particularly from sophisticated phishing attacks and brute-force attempts. This blog post will dissect the concept of passwordless authentication in Microsoft Entra (Azure AD), elucidate its mechanisms, expound upon the compelling advantages of mandating passwordless authentication, outline potential drawbacks, and furnish comprehensive procedural guidance for its implementation within your Azure AD environment.
Modern Authentication Methods
In lieu of conventional narrative constructs, it is imperative to elucidate the progression of contemporary authentication methodologies. Historically, user access hinged on the deployment of usernames and passwords, which, over time, manifested vulnerabilities stemming from password complexity requirements and user susceptibility to credential-based breaches.
Contemporary authentication methods have emerged to surmount these challenges, embracing multi-factor authentication (MFA), biometrics, and security tokens. Among these, passwordless authentication emerges as an especially promising paradigm, effectively eliminating the dependence on passwords.
The Mechanics of Passwordless Authentication in Microsoft Entra
Microsoft Entra (Azure Active Directory), the cloud-based identity and access management solution from Microsoft, offers robust support for passwordless authentication, which can be comprehended through the following mechanisms:
-
Biometric Authentication: Biometric authentication represents a pioneering approach to user verification within Azure AD. This method leverages the inherent and unique physical attributes possessed by individuals, such as fingerprints and facial features, to grant access. By employing biometric data, Azure AD provides a highly secure and nearly foolproof means of authentication. Users simply present their biometric identifiers to unlock their accounts. This eliminates the need for memorizing and managing complex passwords, and it significantly bolsters security by making it exceptionally challenging for malicious actors to impersonate users.
-
PIN-Based Authentication: In scenarios where the adoption of biometrics is not feasible or preferable, Azure AD offers the option of PIN-based authentication. Users can establish personal identification numbers (PINs) associated with their accounts. This PIN serves as a secure alternative to passwords and enhances the ease of access. PINs are shorter and simpler to remember than typical passwords, while still providing a layer of security. Users can confidently access their accounts by entering their unique PIN, streamlining the authentication process while reducing the risk of password-related breaches.
-
Security Keys: For organizations seeking the utmost in security for their Azure AD authentication, hardware security keys represent a formidable choice. These physical devices are designed to provide an additional layer of protection against unauthorized access. Users insert these security keys into their computing devices, and they generate cryptographic keys that authenticate the user securely. By utilizing security keys, organizations can ensure that only authorized personnel with the physical key can access sensitive resources. This method is especially valuable for high-security environments where data protection is paramount.
-
Microsoft Authentication App: The Microsoft Authenticator app introduces a seamless and user-friendly method of passwordless authentication. By installing this app on their smartphones, users can approve sign-in requests with a simple tap. This process is both secure and convenient, as it eliminates the need for traditional passwords or even PINs. When a user attempts to access their Azure AD account, a notification is sent to their Authenticator app. Upon verification of their identity through the app, access is granted. This approach not only enhances security but also enhances user experience by reducing friction during the authentication process.
Each of these passwordless authentication mechanisms in Azure AD represents a formidable step forward in bolstering digital security. By eliminating the dependence on passwords, organizations can significantly reduce the risk of credential-based breaches and enhance user convenience. The choice of which method to implement should align with the organization's security requirements, user preferences, and the specific use cases where passwordless authentication is deployed. Ultimately, the goal is to provide a highly secure and user-friendly authentication experience that safeguards critical digital resources.
Rationale for Enforcing Passwordless Authentication (Advantages)
Mandating passwordless authentication within Azure AD engenders an array of compelling advantages:
-
Elevated Security: Passwordless authentication dramatically mitigates the susceptibility to credential-based attacks by obviating passwords as an attack vector.
-
Resilience Against Phishing: Notably, passwordless authentication inherently resists phishing attacks—a persistent and increasingly sophisticated threat vector in today's threat landscape. By eliminating passwords, passwordless methods counteract user susceptibility to phishing schemes, effectively nullifying phishing's efficacy.
-
User Convenience: Passwordless modalities, such as biometrics and PINs, streamline authentication, offering heightened convenience for end-users.
-
Cost Reduction in Support: The reduced incidence of password-related issues translates into diminished IT support costs and alleviates the burden associated with password resets.
Consideration of Drawbacks
While the benefits of passwordless authentication are substantial, it is prudent to acknowledge potential drawbacks:
-
Device Dependency: Certain passwordless modalities, notably biometrics, and security keys, necessitate specific hardware or devices, potentially limiting universal accessibility.
-
User Adoption: User apprehension and a learning curve are common initial impediments to the adoption of passwordless methods, necessitating effective change management strategies.
-
Contingency Measures: Organizations must devise and implement backup authentication methods to address contingencies, should a user's preferred passwordless method encounter issues.
Step-by-Step Implementation of Passwordless Authentication with Microsoft Authenticator
To initiate the deployment of passwordless authentication within your Azure AD environment, follow these comprehensive procedural steps:
- Access Entra (Azure AD) Portal: Log in to your Entra portal as an administrator.
- Navigate to Authentication Methods: Within the Entra portal, navigate to "Protection" then proceed to "Authentication methods > Authentication method policy."
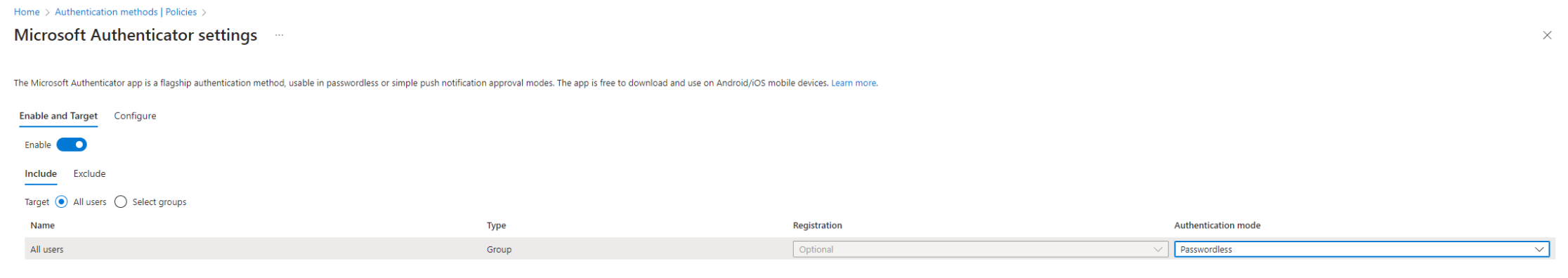
- Enable Passwordless Methods: In the "Authentication methods" section, enable the Microsoft Authenticator policy. It can be applied to all users or security groups. Make sure to select "Passwordless" under Authentication mode".
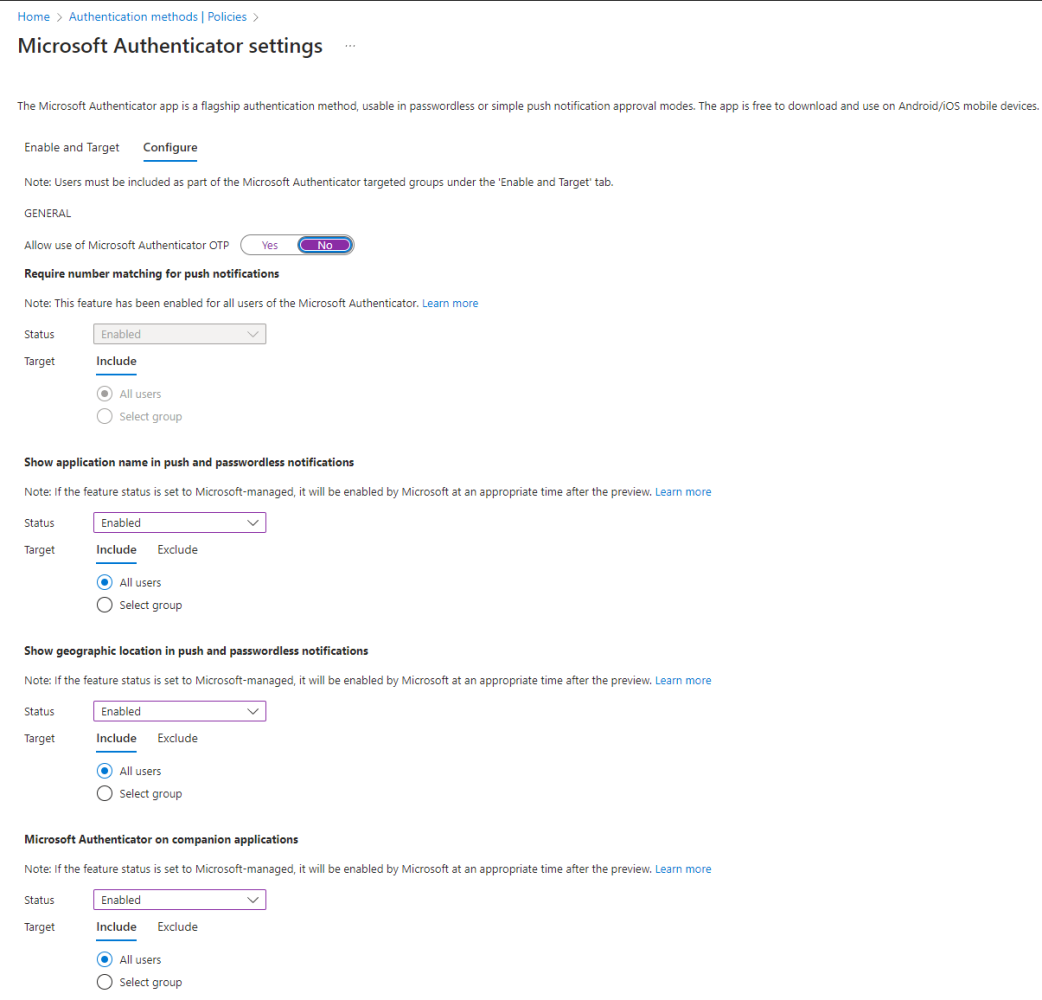
- Set Up Configuration: Tailor user settings for passwordless authentication to show the application name and geographic location in passwordless notifications. Set to enabled. Note: If you leave at default Microsoft-managed, it will be enabled by Microsoft after the preview, so I recommend setting it to enabled immediately.
- Have users register for passwordless sign-in by sending appropriate communication. Users register themselves for the passwordless authentication method of Microsoft Entra ID.
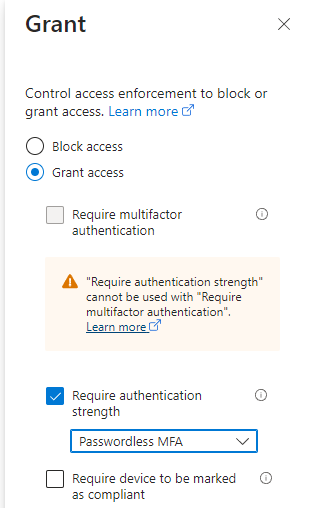
- Enforce Passwordless: In "Entra" select "Protection", and then "Conditional Access" to create a new policy. Craft policies mandating passwordless authentication for specific users or scenarios. Select "Require Authentication strength" -> "Passwordless MFA" as an option.
- This concludes the process.
Conclusion
In summation, advocating for passwordless authentication in Azure AD represents a proactive stance toward fortifying digital security, simplifying user access, and efficaciously mitigating the perils associated with conventional passwords. Notably, this strategic choice offers resiliency against the pervasive and increasingly sophisticated threat of phishing—a threat vector that continues to evolve in tandem with advances in artificial intelligence. Although caveats exist, the gains derived from the adoption of passwordless authentication far outweigh the potential shortcomings. By adhering to the meticulously delineated procedural guide, organizations can confidently embark on a path toward a more secure and user-friendly authentication paradigm.